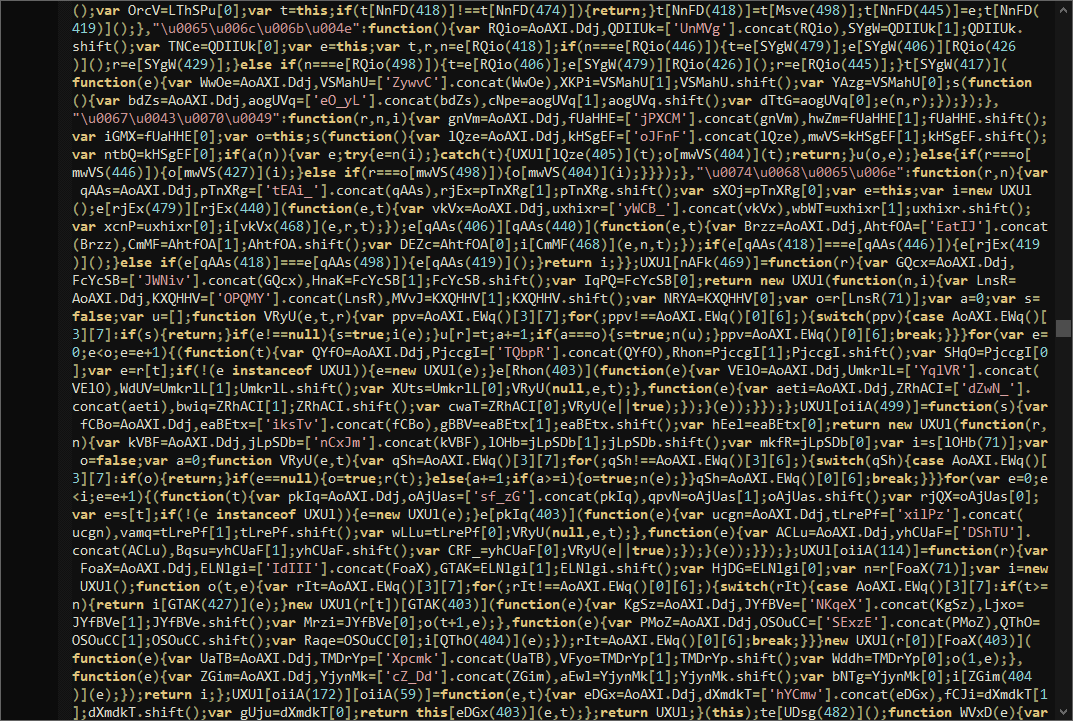
There are several ways to protect the javascript (js) files. A lot of free and paid services. The basic idea is to add trash code and rename the variables/functions names. There is no way to recover the original names of the variables/functions but this is not a problem for a good js developer.
Decrypting is based on executing the obfuscated code and extracting the real string values of the source code. After that, replace the string values in right places and remove the trash code.
Do not confuse encrypted files with minimized files. Minimized js file is the same source code file with no spaces. Sometimes variable/functions names are replaced with simple letters like “a”, “b”, etc. The code is still readable. Anyone can replace these names with suitable and more human names.