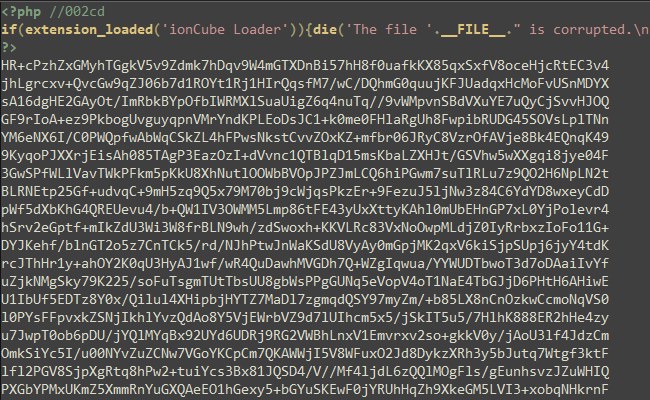
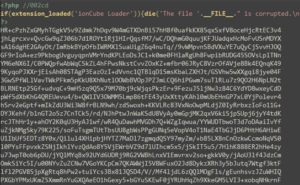
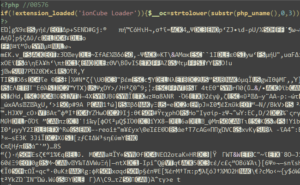
ionCube protects PHP applications by compiling source code into bytecode before encoding it. This process removes the original source code and reduces runtime overhead, making reverse engineering more challenging.
However, there are two primary approaches to recovering the original source code:
1. Reverse Engineering the Entire Encoder
This method is the most reliable — but also the most complex. It involves a complete analysis of the encoded file to extract its operational data. The general steps include:
-
Remove Custom Encodings: If custom base64 encoding has been applied, strip it away to access the raw data.
-
Analyze Header Information: Examine the file headers for embedded license information, external keys, or dynamic keys.
-
Extract Opcodes: Retrieve all embedded classes, functions, and code opcodes from the file.
-
Reconstruct Source Code: Use the recovered opcodes to rebuild the original PHP source code.
2. Patching the ionCube Loader
Another approach involves modifying the ionCube loader itself to intercept and capture opcodes during execution. The steps are:
-
Patch the Loader: Alter the ionCube loader to allow opcode extraction using a custom PHP executable.
-
Capture and Reconstruct: Once the opcodes are captured, reconstruct the source code from them.
Notes on License and Keys
While license files, external keys, and dynamic keys can complicate the decoding process and increase the time required, they do not make the protection fundamentally unbreakable.
I started from here: link_1, link_2.